Some information regarding #APT34:
On the 20th of March 2019, some webshell accounts were offered for sale on RAID FORUMS, some of the offered accounts belonged to:
Published accounts include:
- Abu Dhabi Airports
- Etihad Airways
- Emirates Policy Center
- Nigerian Building & Research Institute
- National Security Agency of Bahrain
- Emirates National Media Company
- Emirates National Oil Company
- Qatar padiwan
- Emirates Federal Competitiveness and Statistics Authority
- Emirates Prime Minister Office
- Lamprell Energy Ltd.
- Abu Dhabi Statistics Center
- Oman Administrative Court
- Kuwaiti Diwan
- SSTC
- Jordan NITC - National Information Technology Center
- Emirates Ministry of Presidential Affairs
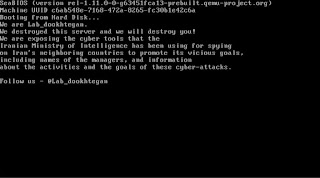
On the 25th of March a channel was created on Telegram under the name of Lab Dookhtegan, after one day, the following paragraph was posted on it:
“We are exposing here the cyber tools (APT34 / OILRIG) that the ruthless Iranian Ministry of Intelligence has been using against Iran’s neighboring countries, including names of the cruel managers, and information about the activities and the goals of these cyber-attacks. We hope that other Iranian citizens will act for exposing this regime’s real ugly face!”
Following that post, there were several posts claiming to expose the identity of some Iranian hackers who are responsible about #APT34, including their CVs, and the tools and techniques used:
- Poison Frog (Similar to Glimpse) – panel, server side and powershell agent (communicates over DNS and HTTP) – all written and used by the group.
- webshell written by the group, uses encrypted RSA communication.
- DNSpionage tool: code used for MITM to extract authentication details (written in python) and code for managing the DNS hijacking.
- Highshell, Hypershell, Minion Project, FoxPanel – webshell codes and their managing panels created and used by the group.
Starting from the same date, 26th of March, there was posts leaking the webshell accounts of the aforementioned entities, these posts were posted consecutively till 6th of April.
On the 20th of April, it was confirmed that a copy of the leaked accounts is available to download as a 7z compressed file hosted on AWS.
It is highly advisable that, all affected entities, should start investigating this issue, and if breach is confirmed, they should start their incident response processes immediately.
If you choose to replace the frame, be sure that you install it correctly so that it will fit snugly into place. If you are curious to know more about chains and cables, browse this site.
ReplyDeleteSome of these companies also offer service for residential or apartment buildings as well. If you are curious to know more about security system company in chicago, read me.
ReplyDeleteThank you for helping people get the information they need. Great stuff as usual. Keep up the great work!!! Complete CCTV Sydney
ReplyDeleteExcellent and very exciting site. Love to watch. Keep Rocking. spy cam
ReplyDeleteTook me time to read all the comments, but I really enjoyed the article. It proved to be Very helpful to me and I am sure to all the commenters here! It’s always nice when you can not only be informed, but also entertained! cctv camera
ReplyDelete